📣 Have you already considered joining our ITOT.Academy ?
We tell stories.
We focus on concepts, not tools.
On frameworks, not features.
👉 Check out our podcast to learn more !
If you’re still thinking of OT cybersecurity as “just” another IT checklist item, it’s time to rethink the whole game. In this episode of the IT/OT Insider podcast, David is joined by Danielle Jablanski — cybersecurity strategist, OT advocate, and all-around force in the industrial cyber world — for a grounded conversation on what cybersecurity in industrial systems really means, why it’s not a product or checklist, and how to approach it without getting lost in the buzzwords.
Danielle brings not only deep knowledge but also practical field insight from her time at CISA, Nozomi Networks, and now STV.
What is OT Cybersecurity Anyway?
OT (Operational Technology) isn’t just ICS (Industrial Control Systems) anymore. “OT now represents a broad set of technologies that covers process automation, instrumentation and field devices, cyber-physical operations, and industrial control systems,” Danielle explains.
From water utilities and power grids to baggage claim systems and digital parking meters, these systems form the backbone of our critical infrastructure. And unlike IT systems, the primary concern isn’t just data breaches—it’s real-world, physical consequences.
“Segmentation is King”
Danielle is clear: “For the last five or six years, I've always said segmentation is king. I still think it's paramount.” But that doesn’t mean it’s easy or one-size-fits-all.
The problem? Too many organizations buy visibility tools but neglect the basics like firewall rules or sound architecture. As Danielle notes, “You can't do any type of root cause analysis if you're not incorporating your entire operation into your purview.”
Her takeaway: start with effects-based thinking. “Focus on the effect of something rather than the means.”
By the way, did you know our very first post on this blog was about the Purdue model? Check it out here:
No More Choose-Your-Own-Adventure Security
Danielle challenges a common trap: jumping into cybersecurity with no strategy. “There’s this leap to: I want a pen test, I want incident response, I want this, this, this. But are people even ready for a 150-page pen test that tells you everything you might want to fix over the next 10 years?”
Instead, she advocates for needs assessments, crown jewel analysis, and understanding fault tolerance. She says, “You need to understand what is impossible, what is not plausible… you can't do that without really getting to root cause analysis.”
The Good, the Bad, and the Pointless Deliverables
When asked about good versus bad deliverables, Danielle doesn’t hold back: “A red flag? People rush to procure tools.” In contrast, green flags are often simple: “What forensic capacity do you have? What logs are you keeping? What’s your retention policy?”
And watch out for this one: “Our integrator is responsible for cybersecurity.” That’s a red flag unless you’ve built a mechanism to test and verify that assumption.
Starting a Career in OT Security
For anyone curious about stepping into the field, Danielle’s advice is encouraging and honest. “You can take any interested person and train them based on their interest and their aptitude.” She recommends free online resources like learn.automationcommunity.com and Grady Hillhouse’s Engineering in Plain Sight.
Her bottom line? “Do whatever you're interested in and do it as much as your resources allow for.”
Why It Matters
Throughout the conversation, Danielle keeps it grounded: OT cybersecurity isn’t about buying the latest tool or chasing the latest threat report. It’s about resilience, design, human capacity, and real-world impact. “All the tools in the world are not going to help you if you haven’t built the scaffolding.”
Or, to put it more bluntly: this isn’t a choose-your-own-adventure.
It’s about picking a strategy and sticking to it.
Let us know what you thought of this episode and if you want more cyber content, get in touch. Like we promised during the episode, this topic is too important and we haven’t touched OT Cyber Sec enough… So we’ll be launching a full cybersecurity series later this year.
Extra Resources
Find Danielle on LinkedIn: https://www.linkedin.com/in/daniellejjablanski/
Free learning: learn.automationcommunity.com
Grady Hillhouse’s book: Engineering in Plain Sight
Copenhagen Industrial Cybersecurity Event : https://insightevents.dk/isc-cph/
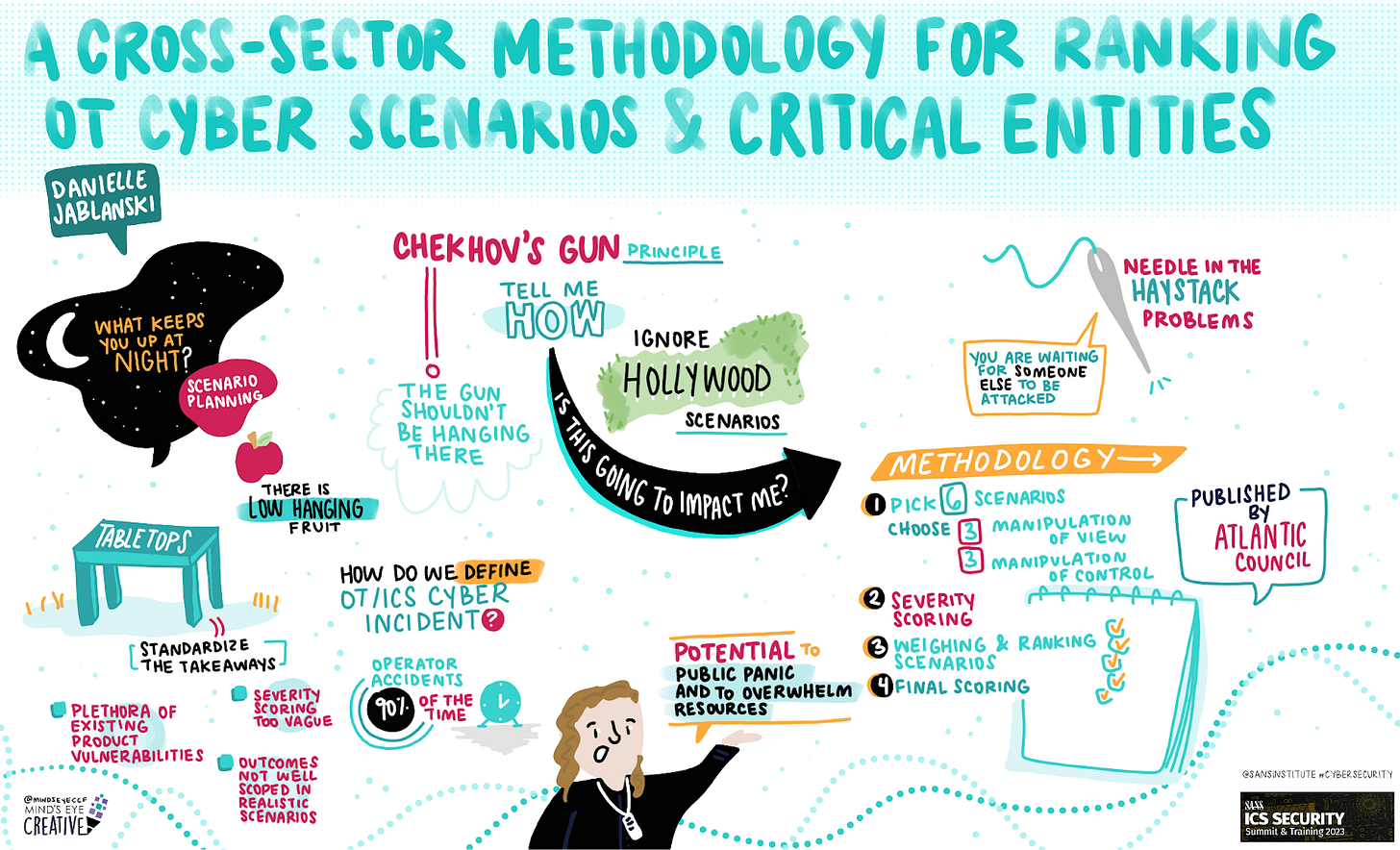
Danielle’s talk at SANS:
And see also https://www.sans.org/blog/a-visual-summary-of-sans-ics-summit-2023/ for this stunning visual summary of her talk:
Stay Tuned for More!
Subscribe to our podcast and blog to stay updated on the latest trends in Industrial Data, AI, and IT/OT convergence.
🚀 See you in the next episode!
Youtube: https://www.youtube.com/@TheITOTInsider
Apple Podcasts:
Spotify Podcasts:
Disclaimer: The views and opinions expressed in this interview are those of the interviewee and do not necessarily reflect the official policy or position of The IT/OT Insider. This content is provided for informational purposes only and should not be seen as an endorsement by The IT/OT Insider of any products, services, or strategies discussed. We encourage our readers and listeners to consider the information presented and make their own informed decisions.













Share this post